Cyber Security and Vulnerability Implementation
4/30/2019
Cyber Security and Vulnerability Implementation
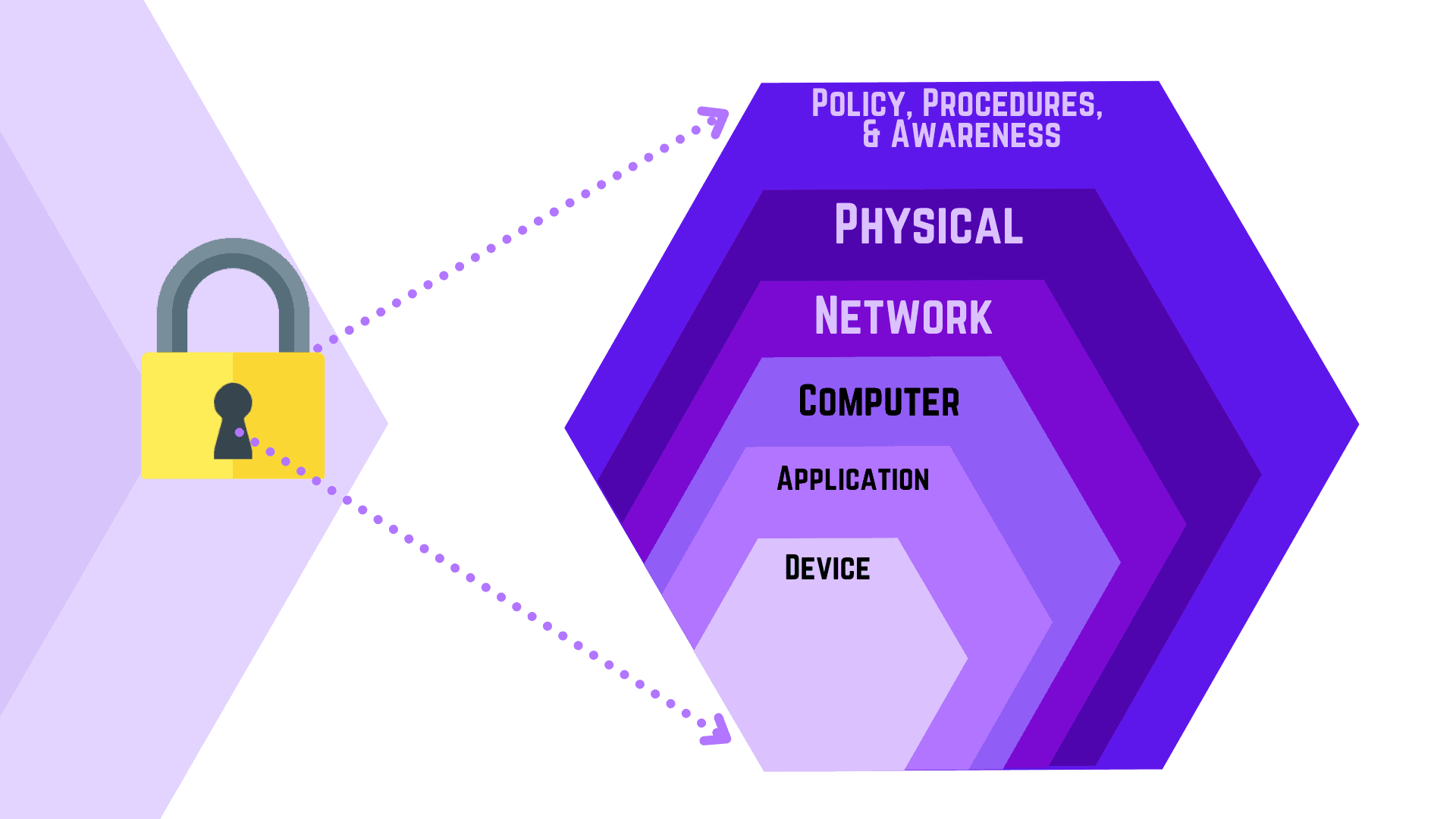
Involved evaluating and implementing best practices to protect a business from internal and external threats.
Delivered the governance process framework for certification of application access and introduced transformation standards. The activities included evaluating and implementing security best practices to protect a healtcare client from internal and external threats.
The goal was to discover any flaw or weakness in system security procedures, design, implementation, or internal controls that could be exercised (accidentally triggered or intentionally exploited) and result in a security breach or a violation of the system's security policy.
4 Steps of the Vulnerability Management Process
- Perform Vulnerability Scan.
- Assess Vulnerability Risk.
- Prioritize & Address Vulnerabilities.
- Continuous Vulnerability Management.
OWASP Top Vulnerabilities:
- Broken Access Control.
- Cryptographic Failures.
- Injection.
- Insecure Design.
- Security Misconfiguration.
- Vulnerable and Outdated Components.
- Identification and Authentication Failures.
- Software and Data Integrity Failures.
PROJECT INFORMATION
Year:
2019
Client:
Quadax Inc.
Date:
Duration:
45 Days
Complexity:
40 out of 100
